 March 4, 2024
March 4, 2024
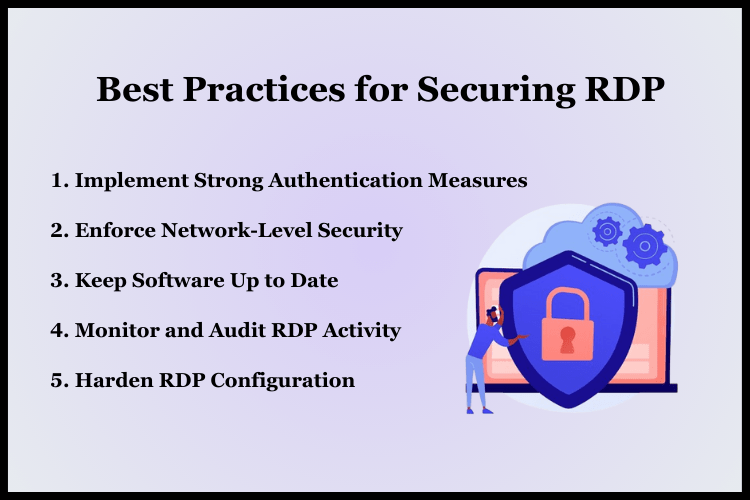
What are the best practices to prevent RDP security issues?
Summary

Article Name
What are the best practices to prevent RDP security issues?
Description
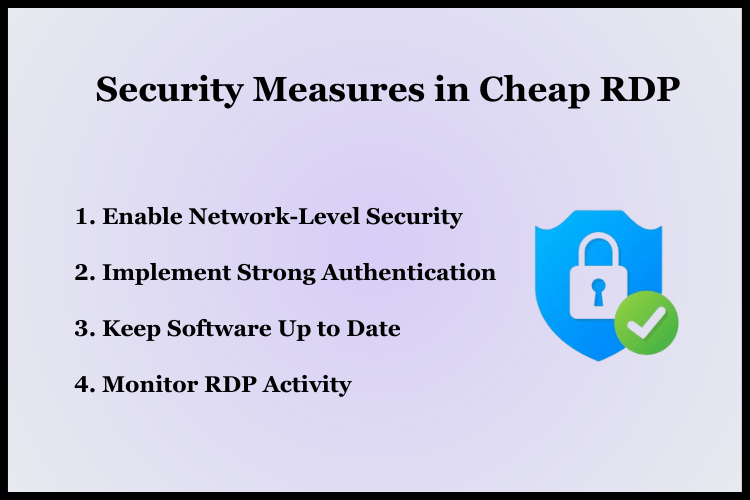
Remote Desktop Protocol (RDP) has become an essential tool for businesses, enabling remote access to computers and systems. It's crucial to implement secure RDP practices while using Cheap RDP Services
Author
Dikshita
Publisher Name
Buy-RDP
Publisher Logo


Leave a comment