 November 3, 2021
November 3, 2021
What is RDP and what kinds of software are not allowed while using RDP?
Summary

Article Name
What is RDP and What Kinds of Software Are Not Allowed While Using RDP
Description
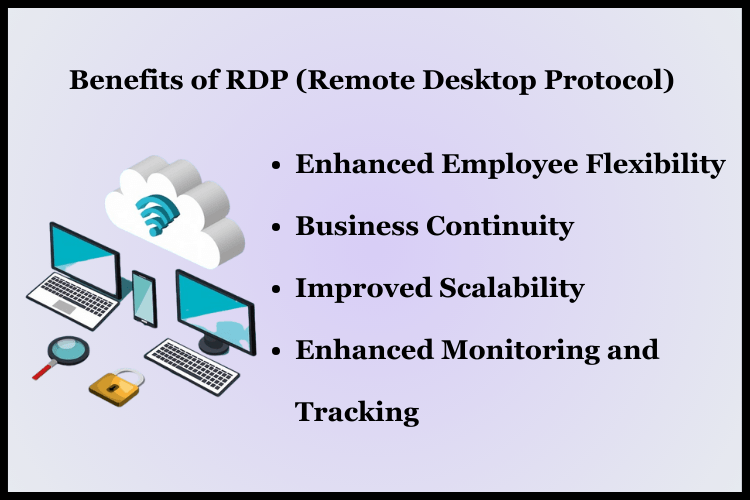
What is a RDP? The term Remote Desktop Protocol (RDP) refers to a proprietary protocol developed by Microsoft, which provides a user with a graphical interface to connect to another computer over a network connection.
Author
Dikshita
Publisher Name
Buy-Rdp
Publisher Logo


Leave a comment